This is a write-up I did after working through this CTF: https://tryhackme.com/room/attacktivedirectory
Tools:
- Impacket:
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (e.g. SMB1-3 and MSRPC) the protocol implementation itself. Packets can be constructed from scratch, as well as parsed from raw data, and the object-oriented API makes it simple to work with deep hierarchies of protocols. The library provides a set of tools as examples of what can be done within the context of this library. - Bloodhound
BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory environment. - Neo4j
Network Exploration and Optimization 4 Java – graph database management system - NMAP
Network scanner - Enum4linux
tool for enumerating information from Windows and Samba systems - Kerbrute
A tool to quickly brute force and enumerate valid Active Directory accounts through Kerberos Pre-Authentication - Hashcat
A hash cracking tool - SMBClient
A tool for enumerating and accessing SMB after you’ve already discovered a valid username/password combo - Secretsdump.py
A tool for dumping password hashes after domain credentials are discovered
Enumeration:
- Add spookysec.local to /etc/hosts file. This allows us to call commands against the domain name instead of the IP address. Some tools prefer domain addresses and it is generally easier to remember rather than using an IP address
- Basic nmap scan. I like to run this one first and then a
nmap -A -p-in the background. The output here is typically pretty fast and I can get started on some other enumeration while I wait for the longer form nmap scan to return.

- Enum4Linux was used here to do some basic AD enumeration. This grabbed some basic information about the Active Directory instance such as the domain name
THM-AD. Nothing super useful here, but it is good enumeration.

- Create a username and password .txt file to do some AD enumerations. I downloaded these from the git repo listed on the box’s page. Just about any password list will do here.
- Run Kerbrute to see if I can find anything interesting. Kerbrute will attempt to log into every account once and check the response. This can tell you if any pre-authentication is required on the domain. For future reference, this box can be *fixed* simply by disabling all pre-auth. This is how foothold is found.

- As we see, svc-admin has a hash with no pre-auth required! We can copy this hash for future use.
- We also found this ser list that might give us some accounts to attempt to crack in the future.

Foothold:
- GetNPUsers.py is built into Impacket and can be used to grab the hash we’ll use to crack the user account. This is just another tool to get the same hash. Hashcat can crack either one, but this is the one I chose to crack. I was playing around with the tools available to me on the box.

- Now time for hashcat! I took the hash I grabbed from
GetNPUsers.pyand dropped into hash.txt. I also used the list of cracked passwords that I grabbed earlier as cracked.txt and ran that into Hashcat. (Ignore my sloppy file organization!)

- According to the hashcat run, the password is:
management2005 - Now that we have domain credentials, we can do some SMB enumeration. We can log into an SMB share with
smbclient

- To me there are a few SMB shares that look interesting. Because we found access to the
svc-adminwhich likely means ‘service admin’ it might be an account to help with backup automation. I was also intrigued by the SYSVOL folder because I’ve found, in the past, plaintext passwords in startup scripts and group policy deployments in there in the past. In this case, nothing good was found.



- This looks like base64? It appears to decode to:
backup@spookysec.local:backup2517860now THIS is the actual backup account!
Root:
- Now that we have the backup user password and we know that this is a backup of the domain controller, we can run the
secretsdump.pytool.

- This outputs the hash for the administrator account:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e0363213e37b94221497260b0bcb4fc::: - Now we can play a little game of “Pass The Hash” to log in as the administrator

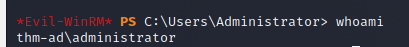

- That is root and flag!