For my Software Security class we were given the task of remediating vulnerabilities in the OWASP Wacko Picko web server. This is an intentionally vulnerable and broken web server with quite a few intentionally bad bits of code. The code for this box can be found here:
https://github.com/adamdoupe/WackoPicko
Problems
Session ID Vulnerability
Definitions [https://cwe.mitre.org/data/definitions/384.html]
This vulnerability is exploitable because the SessionID can be manipulated in such a way that a valid SessionID can be injected into an unauthenticated session and grant that user administrator privileges. The sessionID for this is stored under the `session` token. In this implementation the sessionID is iterative and easily enumerated. If an attacker is able to guess a sessionID of an administrator, they could easily hijack that session and be granted unearned authorization.
CWE General Defense
- Create unique and random session identification strings
- Have a reasonable timeout on sessions to prevent brute force attacks
- Design additional authentication tools into a sessionID that looks for fingerprints of a device such as IP addresses, browser details, or other identifiers.
High-level description of the approach to fix this issue
- Initially the code was written to use a simple integer session ID that iterates starting at 1
- The resolution was to modify the SQL entry to be a varchar string and then in the PHP code use the default php session ID generation code to create a unique ID to write to the cookie of the user and then store into the database.
Snippets of the vulnerable code
Snippets of the fixed code
Demonstration of resolution
As you can see in the following image, the PHPSESSID that is generated is now a unique and unpredictable session ID string value instead of an easy to predict and iterable number.
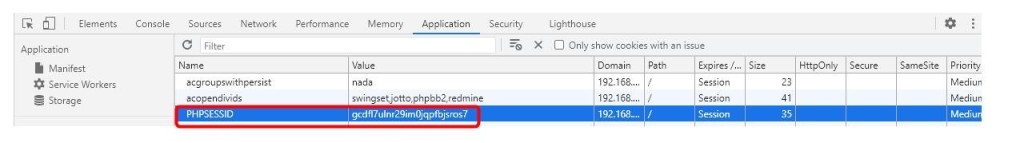 |
Forceful Browsing
Definition [https://cwe.mitre.org/data/definitions/425.html]
In this vulnerability, the pictures are stored in an open directory that allows for easy enumeration. The WackoPicko application allows you to only view the images that you’ve purchased, but during the purchase process, you are given the full address for the file. This can also be viewed in the address bar when viewing the image. It is clear here that the picture ID is captured under the tag picID=8. With basic enumeration, you can view all other images by increment or decrementing that number. The code is not doing proper authentication upon viewing this file.
Defense
- Obscure the file names. Do not make them sequential numbers, but instead randomly generated strings. This protects against primitive attacks and can greatly slow down brute force or fuzzing attacks
- Force authentication always and then, upon loading the image, confirm that authenticated user owns that image.
High-level description of the approach to fix the issues
- Each user has a store of which images they own. You simply need to build an array of those image IDs and check if the image attempting to load is owned by that user.
Snippets of the vulnerable code
Snippets of the fixed code
Demonstration of resolution
As you can see in the following image, browsing to an image that I do not own sends me to a 404 error
 |